- Submissions

Full Text
Research & Development in Material Science
Elliptic Curve Based Server Authentication System for Multi-Server Infrastructure
Himanshu Monga* and Nancy Girdhar
Department of ECE, Lovely Professional University, India
*Corresponding author: Himanshu Monga, Department of ECE, Lovely Professional University and Director of Jan Nayak Chaudhary Devi Lal Lal Vidyapeeth, Sirsa, Haryana 125055, India
Submission: October 02, 2017; Published: November 29, 2017

ISSN : 2576-8840Volume2 Issue3
Abstract
A server authentication scheme for a multi-server infrastructure has been proposed. In this scheme, each member involved in communication has to prove its authentication before any information is exchanged. This scheme secures the servers against phishing and other such attacks. Dynamic properties of the group are handled with ease, making the scheme suitable for real-life applications.
Keywords: Elliptic curve cryptography; Visual cryptography; Multi-Server system; Group communicating server
Introduction
Over the years different authentication schemes have been proposed by the researchers. But most of them are either incompetent or take too much time to respond which makes them useless for real life applications [1]. However, [2-6] have proposed authentication schemes using cryptographic techniques, but the existing schemes are mostly defined for specific type of groups. They provide authentication at user side but not at server side. In practical scenario forgery attacks may occur at server side as well. In this paper we propose an authentication scheme based on elliptic curve cryptography and visual cryptography, to protect the distributed servers form such attacks. Visual cryptography, proposed by Naor & Shamir [5], is a technique, devised for sharing images securely. In visual cryptography scheme, an image is divided into n shares, out of which k shares alone mean nothing, thus protecting the information stored in the image safe [2]. Proposed scheme is appropriate for a multi-server infrastructure in which group of members is connected to one of the many interconnected group communicating servers. Although there exists various multisignature schemes for multi-server infrastructure, but in multisignature schemes there is a fundamental drawback. In those schemes, the authentication center could be exploited by forging the signatures thus those schemes are vulnerable to attacks. Proposed scheme conquers all such forgery attacks as the communicating members provide their identity and also the identity of their group in terms of image shares.
The remainder of the paper is organized as follows: Section 2 describes the multi-server infrastructure, on which the server authentication scheme has been proposed. In section 3, proposed scheme has been discussed. In section 4 we discuss the implementation of system on the basis of our proposal. Section 5 discusses the dynamic alterations and adjustments in the group and in the end section 6 gives the conclusion and future scope.
Multi-server systems
Multi-Server systems generally have distributed servers. In a multi-server system Group Communication Servers and members together constitute groups. Within a group, members are connected to GCS. GCSs of various groups are interconnected and are responsible for all the communication. This scenario is common for Multinational companies or companies that deal with large amount of data [1]. Figure1 shows one such multi-server scheme. In this figure two groups have been shown, their GCSs are connected to each other and each GCS is also connected to four members.
Figure 1: Multi-Server Infrastructure.
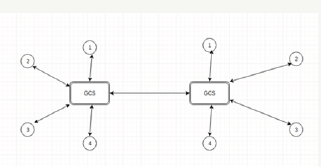
A member can access data from a member of the same group or a member of other group. All the communication, whether it's inter-group or intra-group takes place via GCSs. While communicating GCS acts as a mediator between the involved members, it receives and delivers messages securely on their behalf. In case of inter group communication the members communicate messages to their own GCSs and then the respective GCSs of the involved groups communicate to each other. As all the communication is carried out via GCSs, thus they play an important role in the security and information exchange. Various priority algorithms are used at GCSs so as to make sure there are no prolonged delays in data delivery.
Proposed scheme
Proposed scheme works as follows: Let's assume, a member of the group1 wants to communicate with a member of group2. So he will contact his server, let's call it GCS1. Now GCS1 asks the member to authenticate it. After verifying the identity of the member, GCS1 gets itself verified. After this entire authentication GCS1 informs the other GCS, say GCS2 and all the other members of his own group. Each and every member involved in the communication authenticates itself and provides his share of the group's proof of authenticity that is group’s image share. GCS uses the individual image shares to generate a group verification image share [6]. This image share is validated by other GCS and all the group members. This way both the groups authenticate each other.
This scheme works on the assumption of there being a public directory that stores verified image shares of all different groups. The concerned party can verify the authenticity by overlapping the public share over the received share, and if product is uniform original image then the group is said to be genuine, and if the image is distorted from any part then group is said to be compromised and connection is broken. Elliptic curve cryptography plays an essential role in member- -server authentication procedure to keep the image shares secure. Elliptic curve cryptography was introduced by Koblitz [7] and Miller [8] in 1985.
All the distributed servers are placed such that, they give the impression that they have been placed on an elliptic curve and the main calculation associated is in performing the operation
Q=nP
Which is the equivalent to the addition of p to itself n times. Here Q and P are the points on the curve and n is an integer known as the scalar multiplier. Security of the procedure is proportional to the infelicity of determining n from Q=nP, provided Q and P, this problem is known as elliptic curve discrete logarithm problem [6]. This is because of the fact that addition of two points on an elliptic curve yields another point on the same elliptic curve.
System set up and initialization
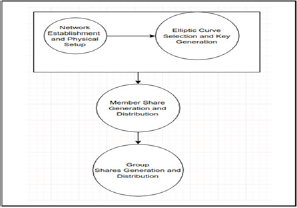
GCSs are set up and are interconnected to each other thus a network of servers is established. Group members are connected to GCSs. An elliptic curve is chosen with a generator g having large prime order q, along with some additional parameters. Individual public and private keys are conceived all members including GCSs. These keys are used for intra-group authentication purposes. After that a group key for group identification and authentication is created and is stored on a public directory. This key is used for inter-group authentication.
An elliptic curve having a point g as its generator is elected, and a one-way hash function H (.) is chosen.
Each member elects a random integer let 'a' as its private key where value of a may vary from 0 to q-1, where q is the order of elliptic curve for that particular group.
Using the elliptic curve discrete logarithm equation Qa=aP, Each member generates its public key Qa and broadcasts it. Similarly Each GCS elects his private key assume 'b', uses this to generate public key let Qb and then broadcasts the public key. Now, group public key 'Q' is calculated by adding all the previously generated keys.
For a member to be able to identify it, it needs to have some sort of identity proof. In our scheme a member creates his own identity in the form of an image share. Each member including GCS chooses an image of his will and creates two shares of the image using visual cryptography. Each member distributes one share along with the original image to all the other members of the same group. While distributing the shares they are encrypted using public keys of the receivers. Group members keep the received shares and images private. These personal image shares are used for authentication purpose later in the communication.
For a group to communicate with another, it needs to prove its authenticity to another group. In order to prove its authenticity a group needs to have an identity proof, which authenticates the whole group at once. So as to achieve that during setup phase GCS chooses an extra image. This image is approved by each and every member of the group before being put to use. After the image is approved, GCS creates n+1 shares of the chosen image (where n is number of members in the group including the server). One share is uploaded onto the public directory and rests of the shares are distributed in the group, one to each member.
Prototype implementation
Figure 2: System Set Up and Initialization.
Main factors that vouch for our design are, the feasibility of the system, ease of installation & use, and less cost of computation.This authentication scheme can be tested upon home computers, by operating them as servers. Figure 2 shows a group structure from a multi-server system with two GCSs where each GCS have two members. Scheme works as:
First a member of group1, say M1 wants to communicate with member m4 of group2, so it informs the server (GCS1) of the communication it wants to make. GCS1 asks the member to authenticate his identity. M1 transfers his share of the image encrypted using GCS1's public key and asks the GCS1 to authenticate himself. GCS1 after receiving the image share decrypts it using his private key and then the two shares, one received now and the other that was given to the receiver during setup phase, are stacked transparently and in a way that their pixels align properly to generate the original image [4].
If the previously sent image and the reproduced image reckoned to be same then the sender is said to be authenticated. After authenticating the member GCS1 forwards the member his image share encrypted using M1's public key and forwards M1's share to all the other members to inform them of the communication that's about to occur. M1 authenticates the GCS1 in exactly same manner. After the entire authentication GCS1 asks the members to transfer their share of the group's image. After receiving those shares GCS1 overlaps them with his share and generates one single share from those n shares then encrypts it using the other GCS’s say GCS2's public key and transfers it over to prove its authenticity and asks GCS2 to authenticate his group. GCS2 follows the exact same procedure and proves group's authenticity. After the authenticity has been proven further communication takes place. Computation cost of the scheme can be calculated by calculating the cost at a node as except the share stacking process all other steps are common to all members (Figure 3).
Figure 3: Prototype Implementation.
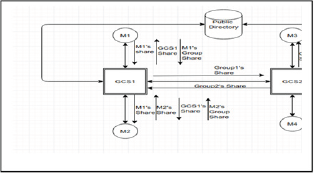
Table 1: Computation Cost.
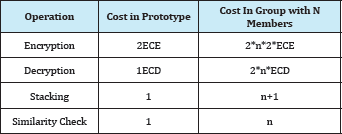
In Table 1, ECE stands for Elliptic Curve Encryption, ECD represents Elliptic curve decryption and stacking represents overlapping operation and similarity check represents image recognition operation.
Handling dynamic property of the group: As the groups are not static, some members may leave and some new may join, so any proposed scheme must be able to handle these scenarios and dynamic property of the group [1].
New addition to the group: Let a new member is added to the group at some point of time. When any new member joins the group setup procedure is called again. In this phase GCS of the group asks the member to create his identity, and create a member share. Member also generates his public and private keys. After receiving image share and image from new member, every other member including GCS gives his share of the image to the new member along with their original images. The group image is also changed; GCS chooses a new image, creates shares accordingly and passes them all to the group members. GCS also changes the share stored at public directory.
Member leaving the group: When a member leaves the group every other member including GCS deletes both, his share of the image and the originally received image. GCS also changes the group image. GCS chooses a new image. Creates share according to the number of members in the group after the modification, transfers the new shares to the members and then changes the share at the public directory.
Conclusion
An authentication scheme has been proposed for multi-server has been proposed. Each member needs to prove its authenticity twice, once as an individual and later as a group member, thus making sure no intruder could break the security by forging someone's identity. Dynamic properties of the groups are handled with utmost ease, ensuring the real life applications of our authentication scheme.
References
- Sankar S, Kalaignan GP, Subramanian S, Amutha K, Marikkannu KR, et al. (2006) Innovative nanoparticle clear coat by ipn-ceramic pigments, synthesis and reactivity in inorganic. Metal-Organic and Nano-Metal Chemistry 36(2): 197-201.
- Vert R, Carles P, Laborde E, Mariaux G, Meillot E, et al. (2012) Adhesion of ceramic coating on thin and smooth metal substrate: a novel approach with a nano structured ceramic interlayer. Journal of Thermal Spray Technology 21(6): 1128-1134.
- Kuznetsov NT, Svast’yanov VG, Simonenko P (2010) Finely dispersed refractory compunds for high-temperature ceramic matrix composite applications. Russian Journal of General Chemistry 80(3): 658-665.
- Greer J (2014) Ceramic nanomaterials that are light, strong and spongy. News & analysis materials news, 39.
- Chichkan’ AS, Chesnokov VV, Gerasimov EY, Parmon VN (2013) Production of nanoporous ceramic membranes using carbon nanomaterials. Doklady Physical Chemistry 450(2): 135-137.
- Moustafa EM, Dietz A, Hochsattel T (2013) Manufacturing of nickel/ nanocontainer composite coatings. Surface & Coatings Technology 216: 93-99.
- Biedunkiewicz A (2011) Manufacturing of ceramic nanomaterials in Ti-Si-C-N system by sol-gel method. Journal of Sol-Gel Science and Technology 59(3): 448-455.
- 8. Johnson SM (2013) Nanoscale ceramics: environmental, health, and safety (EHS) implications. Applied Ceramic Technology 10(4): 577-583.
- Lu Y, Chen F, An P, Ye L, Qiu W, et al. (2016) Polymer precursor synthesis of TaC-SiC ultrahigh temperature ceramic nanocomposites. The Royal Society of Chemistry 91.
- Gao W, Li Z, He Y (2012) High temperature oxidation protection using nanocrystalline coatings, The University of Auckland, New Zeland and University of Science and Technology, Woodhead Publishing Limited, Beijing, China.
- Zheludkevich ML, Tedim J, Ferreira MGS (2012) 'Smart” coatings for active corrosion protection based on multi-functional micro and nanocontainers. Electrochimica Acta 82: 314-323.
- Pivinskii YE, Grishpun EM, Gorokhovskii AM (2015) Engineering, manufacturing, and servicing of shaped and unshaped refractories based on highly concentrated ceramic binding suspensions. Refractories and Industrial Ceramics 56(3): 245-263.
- Tonello K, Trombini V, Bressiani AA, Bressiani JC (2012) Ceramic processing of nbc nanometric powders obtained by high energy milling and by reactive milling. Materials Science Forum, Trans Tech Publications, Switzerland.
- Dey S, Drazin JW, Wang Y, Valdez JA, Holesinger TG, et al. (2015) Radiation tolerance of nanocrystalline ceramics: insights from yttria stabilized zirconia. Scientific Reports, doi:10.1038/srep07746.
- D’Amato R, Falconieri M, Gagliardi S, Popovici E, Serra E, et al. (2013) Synthesis of ceramic nanoparticles by laser pyrolysis: From research to applications. Journal of Analytical and Applied Pyrolysis 104: 461-469.
- Fonseca AS, Maragkidou A, Viana M, Querol X, Hameri K, et al. (2016) Process-generated nanoparticles from ceramic tile sintering: Emissions, exposure and environmental release. Science of the Total Environment 565: 922-932.
- Castro RHR (2013) On the thermodynamic stability of nanocrystalline ceramics. Materials letters 96: 45-56.
- Muktepavela F, Grigorjeva L, Kundzins K, Gorokhova E, Rodnyi P (2015) Structure, nanohardness and photoluminescence of ZnO ceramicsbased on nanopowders. Royal Swedish Academy of Sciences 90(9).
© 2017 Himanshu Monga, et al. This is an open access article distributed under the terms of the Creative Commons Attribution License , which permits unrestricted use, distribution, and build upon your work non-commercially.
 a Creative Commons Attribution 4.0 International License. Based on a work at www.crimsonpublishers.com.
Best viewed in
a Creative Commons Attribution 4.0 International License. Based on a work at www.crimsonpublishers.com.
Best viewed in 







.jpg)






























 Editorial Board Registrations
Editorial Board Registrations Submit your Article
Submit your Article Refer a Friend
Refer a Friend Advertise With Us
Advertise With Us
.jpg)






.jpg)














.bmp)
.jpg)
.png)
.jpg)










.jpg)






.png)

.png)



.png)






