- Submissions

Full Text
COJ Robotics & Artificial Intelligence
Comprehensive AI-Powered Strategies for Enhancing IoT Device Security: Tackling Challenges and Exploring Innovations
Masoud Hayeri Khyavi1*, Niloufar KarimiAzar1 and Mohammad Karami2
1IT Department, ICT Research Institute (ITRC), Iran
2EE Department, Amirkabir University of Technology, Iran
*Corresponding author: Masoud Hayeri Khyavi, Department of Information Technology, ICT Research Center, Iran
Submission: March 03, 2025;Published: May 16, 2025

ISSN:2832-4463 Volume4 Issue4
Abstract
By providing a giant network of interconnected objects that can collaborate and interact in real-time, the Internet of Things (IoT) is regarded as an important step toward technical growth. Nonetheless, given the limitations in resources and the diverse nature of IoT devices, their fast proliferation has led to significant security challenges. The present investigation aims to examine AI-driven tactics in order to enhance the security of IoT devices with a specific focus on deep learning and machine learning techniques. This paper attempts to analyze the existing IoT security solutions comprehensively, address the role of AI in the mitigation and detection of threats, and present future research goals. The present paper aims to present an in-depth investigation and suggest a strategic pathway for using artificial intelligence to increase the security of IoT networks against newly emergent threats.
Keywords:Internet of things; IoT security; Artificial intelligence; Machine learning; Deep learning; Threat detection; Cybersecurity
Introduction
The expansion of the Internet beyond conventional computing devices to a wide range of everyday objects has fundamentally transformed the interaction between people and technology, with the concept of the Internet of Things (IoT). This development has led to advances such as the emergence of smart cities, industrial automation, and smart homes. However, along with these developments, significant security risks have emerged due to the diversity of operational contexts and inherent vulnerabilities of these devices. Traditional security methods are unable to solve such challenges, and the need to use innovative technologies such as artificial intelligence to enhance IoT security is clearly felt [1].
Artificial intelligence is an effective approach to countering cyber threats, such as malware, and has the ability to analyze huge amounts of data in real time to identify and mitigate security risks using Deep Learning (DL) and Machine Learning (ML) techniques [2]. The capabilities of AI have made this technology an effective solution for strengthening security in IoT devices. With the advent of the Internet of Things (IoT), the digital world has been elevated to a new level of interaction between humans and technology. From smart devices that have become an integral part of our lives, to cities and industries that promise a smart and connected future, this technology has not only provided unprecedented efficiency but also convenience. But behind these brilliant developments, there is also a shadow of widespread security risks. IoT devices, with all their advantages, may become a weakness of modern systems due to the failure to adapt traditional security methods to their specific needs [3].
With the advancement of methods such as deep learning and machine learning, AI can identify and minimize potential threats at an impressive speed. This paper attempts to explore the methods that can be used to address specific security concerns associated with IoT devices using AI. In addition to providing a comprehensive analysis of various AI-based approaches, this research also evaluates the success of these approaches. The main focus of the paper is to identify the strengths and weaknesses of AI-based security approaches and to provide suggestions for improving these approaches in the future.
Overview of IoT Security Challenges
Due to a number of reasons, IoT devices are characterized by
problematic security:
A. Resource constraints: A great number of IoT devices
suffer from constrained computing resources, e.g., memory,
storage, and processing power, which make the installation of
resource-intensive security measures difficult, leading to their
vulnerability to cyber assaults [4]. In addition, given that a
great number of IoT devices suffer from low power supply, the
application of standard security measures requiring constant
processing and monitoring is subjected to limitations [5].
B. Heterogeneity: One may define IoT ecosystems as a set of
diverse range of devices characterized by different operating
systems, communication protocols, and designs. Such
variation restrains the use of standard security solutions, and
maintaining the complete security of the network becomes
difficult [6]. Different devices, ranging from complicated
industrial machinery to basic sensors, may need customized
security options. This leads to more complicated IoT security
management [7].
C. Scalability: The significant scaling issues of IoT devices are
due to their sheer quantity. The scalability of conventional
security options may not suffice to resolve the necessities
of developing IoT networks. This may potentially lead to the
creation of security holes [8]. In addition, due to the dynamic
nature of IoT settings, in which different devices are often
withdrawn/added, adaptive security solutions are needed
with the capability of growing with the network [9].
D. Privacy concerns: The fact that private personal information
and business-related data are typically collected by IoT devices
raises important privacy concerns. One of the key challenges
is to ensure that the data are safely stored, transferred, and
collected while the privacy rights of users remain secured.
Given that illegal accessibility to personal information may
lead to far-reaching effects, privacy is regarded as an issue
with utmost importance in IoT security [10].
E. Trust: In IoT systems, trust and confidence management
should be considered as critical issues in order to maintain
secure and reliable interactions between people and devices.
Effective trust management frameworks can cover various
trust-related issues, such as data integrity, user assurance, and
device reliability. Balancing privacy and trust is a challenging
task because maintaining openness for accessibility while
protecting user information requires complex and precise
approaches, for example, anonymization [11]. Additional
issues and challenges may arise in situations such as edge
computing environments, where trust must be managed
across remote systems [12].
F. Digital forensics: In the IoT, digital forensics is a critical issue
for the analysis of security breaches by linked devices. This
necessitates gathering and analyzing information from a great
number of IoT devices. It may become a challenging task due
to the limitations and diversity of devices [13]. Forensic data
analysis is tasked with the reconstruction of the events and
identification of all malicious activities by employing methods
such as pattern recognition and chronology analysis [14]. In
order to verify the acceptability of evidence, it is necessary to
maintain legal compliance, which involves respect for privacy
standards and complete recordkeeping [15].
Using AI-Driven Approaches to IoT Security
AI-based approaches are creatively addressing many of the security concerns that IoT devices face. In this section, we briefly introduce various AI-based strategies for use in enhancing IoT security.
Machine learning for the detection of anomalies
One of the important aspects of IoT security is the anomaly
detection. This is because it includes the detection of deviations
from typical activities that may constitute a security issue. One
may use machine learning algorithms to detect these abnormalities
through learning by referring to earlier data and the recognition of
the patterns that may indicate potential assaults [16].
a) Supervised learning: In supervised learning methods,
labeled datasets with known outcomes are used in order to
train models. By employing the attributes obtained from the
data, it becomes possible for the algorithm like Support Vector
Machines (SVMs) and Random Forests to discern normal
network traffic from abnormal traffic [17]. In settings in which
labeled attack data are limited, such techniques can be limited.
This is because they demand huge amounts of labeled data for
the purpose of training.
b) Unsupervised learning: Given that unsupervised learning
approaches do not demand labeled data, they are helpful
for the identification of unknown or new dangers. Without
earlier knowledge of the attack types, techniques such as
k-means clustering and Principal Component Analysis (PCA)
can detect outliers and patterns in data [18]. Such methods
are particularly helpful for the discovery of new dangers that
otherwise could not be detected.
c) Ensemble learning: In ensemble learning, by combining a
number of machine learning models, the overall performance
and accuracy are improved. The methods such as bagging,
stacking, and boosting can enhance the anomaly detection
systems’ resilience by using the benefits of a number of
algorithms [19]. Ensemble techniques are capable of increasing
detection accuracy and offering a more complete perception of
network dynamics.
An important aspect of IoT security is anomaly detection.
This is important because it involves detecting deviations from
normal activity that may indicate a security issue. Machine learning
algorithms can be used to detect these anomalies by learning from
previous data and recognizing patterns that may indicate potential
attacks [16].
a) Supervised learning: In supervised learning methods, labeled
data sets with known outcomes are used to train models. Using
features obtained from the data, algorithms such as Support
Vector Machines (SVMs) and random forests can be used to
distinguish normal network traffic from abnormal traffic [17].
In settings where labeled attack data is scarce, such techniques
can be used. This is because these algorithms require large
amounts of labeled data to train.
b) Unsupervised learning: Since unsupervised learning
approaches do not require labeled data, they are useful for
identifying unknown or novel threats. Without prior knowledge
of attack types, techniques such as k-means clustering and
Principal Component Analysis (PCA) can identify outliers and
patterns in the data [18]. Such methods are particularly useful
for detecting new and unknown threats.
c) Ensemble learning: In ensemble learning, by combining a
number of machine learning models, the overall performance
and accuracy can be improved. Methods such as bagging,
stacking, and boosting can increase the flexibility and
resilience of anomaly detection systems by taking advantage
of the advantages of a number of algorithms [19]. Ensemble
techniques are able to increase the accuracy of detection and
provide a more complete understanding of what is happening
in the network.
Deep learning for prediction of threats
Deep learning models, particularly Recurrent Neural Networks
(RNN) and Convolutional Neural Networks (CNN), can effectively
process complex data and predict potential threats. Such models
are able to detect subtle patterns in large data sets and adjust as
attack vectors change.
a) Convolutional Neural Networks (CNN): These networks are
suitable for analyzing image and spatial data and are used to
identify patterns and features in the input data. Convolutional
networks are able to extract hierarchical features from raw
data using a large number of layers of convolutional filters.
This increases the accuracy in detecting complex attacks.
Studies have shown that CNNs outperform standard learning
techniques in a number of cybersecurity applications.
b) Recurrent Neural Networks (RNNs): These networks,
especially Short-Term Memory Networks (LSTMs), are tasked
with managing sequential data and are very effective for
evaluating time-series data received from IoT devices. These
networks are able to model temporal relationships and identify
trends in network traffic and can detect persistent attacks.
Long-term short-term memory networks are very useful in
retaining data over long periods, making them effective for
identifying complex attack patterns.
c) Generative Adversarial Networks (GANs): These networks
consist of two neural networks-discriminative and generativethat
compete with each other to improve performance. These
networks are able to generate artificial attack scenarios and
improve the training dataset, which allows for the creation of
stronger security models. GANs also improve security model
generalization and the training process by simulating different
attack scenarios.
Reinforcement learning for adaptive security
Using Reinforcement Learning (RL), adaptive security systems
can be created that evolve and learn based on their interactions
with the environment. Reinforcement learning agents are able to
optimize security techniques and rules through trial and error,
which continuously increases the efficiency of such systems [20].
a. Model-free RL: In model-free RL approaches, for example,
Deep Q-networks (DQNs) and Q-learning, optimal policies are
developed without the need for an environmental model [21].
These approaches can be used in dynamic security contexts
where the agent can learn through direct feedback and
interaction. Model-free RL is best suited for contexts with high
uncertainty and variability.
b. Model-based RL: In model-based RL, a model of the
environment is learned that is used to plan and simulate actions
[22]. Such a technique could be useful for IoT security, as it
enables policy optimization and proactive threat mitigation
based on simulated scenarios. Model-based RL increases
the efficiency of the decision-making process and adapts to
evolving security risks.
c. Multi-Agent RL: A great number of RL agents are included
in Multi-Agent Reinforcement Learning (MARL) that work
together in order to reach a shared objective. Regarding IoT
security, one can use MARL to coordinate the activities of a
variety of devices to jointly fight against threats. Thanks to
collaborative learning, MARL enhances the IoT networks’
robustness [23].
Case Studies
The present section contains a variety of case studies giving practical viewpoints into the execution and effectiveness of the security measures of AI-driven IoT devices and depicting realworld difficulties, solutions, and applications for the purpose of IoT security. We hope to present the practical effect of a variety of trust management approaches, security measures, and digital forensics methodologies through the study of various tactics and scenarios. Such examples present invaluable lessons and emphasize the everchanging environment of IoT security, showing how one can use theoretical basics in real scenarios and the real-world impacts of various approaches.
Smart home security
As an important use of AI-powered security solutions, smart
homes include various IoT devices, e.g., security cameras, lighting
systems, and smart thermostats. AI techniques have been utilized
in order to monitor and defend such network devices against
various dangers.
A. Deep learning for the detection of intrusions: A study by
Haddadpajouh et al [24]. reviewed the use of deep learning
models for the detection of intrusions in smart home scenarios.
The authors utilized an RNN so as to monitor the network data
and spot malicious activities with high precision [25]. Such
a strategy significantly enhances the detection of complex
assaults in comparison with the currently used techniques.
B. Federated learning for privacy preservation: In order
to resolve privacy concerns, smart home security employs
federated learning, which enhances security and, at the
same time, protects users’ privacy by training models on
decentralized data collected from a variety of devices [26].
Such an approach enables collaborative learning without
the need to disclose sensitive data, which makes it a suitable
alternative for the purpose of privacy-sensitive situations.
Industrial IoT (IIoT)
Industrial Internet of Things (IIoT) systems, which include
critical infrastructures such as energy and manufacturing systems,
face specific security concerns. These concerns are compounded
by the high importance of these infrastructures and the potential
impact of cyber-attacks on them. To address these challenges, AIbased
security frameworks have been developed to secure IIoT
networks against cyber-attacks.
a) Machine learning (ML)-based anomaly detection
in industrial control systems: One of the important
applications of AI in IIoT is the use of machine learning-based
anomaly detection to protect Industrial Control Systems
(ICS). Researchers are using ML approaches to detect unusual
activities in ICS networks, which helps identify potential
risks and reduce downtime [27]. This technique significantly
improves the reliability and security of industrial processes
and enables rapid response to threats.
b) Deep learning for predictive maintenance: DL models are
also widely used for predictive maintenance in IIoT contexts.
These models can analyze sensor data to predict equipment
failures and identify potential vulnerabilities before equipment
is deployed [28]. Using this proactive strategy not only helps
prevent costly downtime, but also maintains the integrity of
industrial systems.
AI Methods for Specific IoT Security Challenges
The present section explores the AI techniques geared to resolve specific IoT security challenges on the basis of the overview presented in the second chapter. By focusing on resource heterogeneity and constraints, we aim to show how advanced solutions in artificial intelligence can enhance the efficiency and security of IoT systems.
Resource Constraints
Since Internet of Things (IoT) devices typically have limited
processing capabilities, it is difficult to implement comprehensive
security measures on these systems. This limitation in computational
resources can become a major challenge in protecting the security
of devices and sensitive data. To address these issues, researchers
have developed lightweight AI methods and algorithms that are
specifically designed for use in resource-constrained environments.
A. Lightweight machine learning algorithms: Lightweight
Machine Learning (ML) algorithms, such as linear classifiers
and decision trees, are designed to provide high performance
on devices with minimal resources. These algorithms are
employed to balance resource utilization and optimal
performance. Thus, they can enable the implementation of
strong security measures without imposing additional burden
on constrained systems [29].
B. Edge computing: Edge computing is also a key solution in IoT
security. In this model, data is processed close to the source,
i.e. on the edge devices themselves. This helps reduce the
need for frequent communication with central servers. By
implementing AI models on edge devices, real-time threat
detection and response is possible, eliminating the need for
centralized processing [30]. In addition, edge computing helps
increase the scalability and efficiency of IoT security solutions.
By processing data closest to the source, the time is almost
dramatically reduced and threats can be responded to quickly.
Heterogeneity
Due to the diversity of IoT devices, it is difficult to use
standardized security measures. The AI techniques, e.g., multi-task
learning and transfer learning, present solutions for monitoring
heterogeneity and safeguarding consistent security across various
devices.
A. Transfer learning: Transfer learning makes it possible to
apply the models developed in one domain to another domain.
Such a technique is effective in applying pre-trained security
models to new IoT settings with little additional training
[31]. It is also helpful in overcoming the difficulties caused
by heterogeneous IoT networks through the exploitation of
available knowledge.
B. Multi-Task learning: Multi-task learning includes teaching a
single model in order to carry out a great number of associated
tasks simultaneously. One may use multi-task learning in IoT
security to manage a great number of security challenges, e.g.,
intrusion prevention and anomaly detection, by employing a
unified model [32]. Such a technique improves the efficacy and
efficiency of security measures.
Real-time detection of threats
To mitigate risk and prevent attacks, it is essential to use
real-time threat detection in cybersecurity. Artificial intelligence
techniques, especially stream processing and online learning, can
be effectively used to evaluate data in real time and respond quickly
to threats.
A. Online learning: Online learning algorithms are designed
to handle inputs incrementally and modify and update the
model upon receiving new data. This technique is particularly
effective for IoT systems where threats are constantly
changing. In this way, it allows for adaptation to evolving risks
and continuous monitoring of the security situation. Through
online learning, systems can respond quickly and effectively to
threats and identify security issues before a crisis occurs [33].
B. Stream processing: Stream processing frameworks such as
Apache Flink and Apache Kafka are powerful tools for analyzing
continuous streams of data sent from IoT devices to servers.
These networks, especially when combined with artificial
intelligence models, provide the ability to detect and monitor
security threats in real time [34]. Using such capabilities, the
ability to detect and respond to attacks in a timely manner
increases, and the necessary preventive measures can be
taken. Given the proliferation of cyber threats and their
increasing complexity, the use of artificial intelligence methods
for real-time threat detection seems essential as a key solution
in IoT security. These technologies not only help increase the
efficiency of data protection, but can also lead to the creation
of intelligent protection systems that remain up-to-date and
vigilant.
Privacy and Ethical Considerations
The use of AI in IoT security poses fundamental privacy and
ethical challenges. Protecting user rights and maintaining social
trust requires ensuring the proper and effective implementation
of AI-based security measures. This requires the development and
implementation of comprehensive legal and ethical frameworks
that help balance the utility of technology with the individual rights
of users.
A. Privacy-preserving methods: Privacy preservation, as one of
the fundamental challenges in IoT security, requires innovative
and efficient approaches. Techniques such as federated
learning and differential privacy are specifically designed
to secure sensitive information. In differential privacy, it is
ensured that individual data points are not identifiable in real
terms, meaning that user information is not disclosed in the
analysis process. In addition, federated learning provides an
approach to collaboratively train machine learning models in
which each user’s raw data is preserved without the need to
transfer or disclose it. These methods are especially necessary
in sensitive environments such as IoT where a lot of personal
data is generated and can help to enhance user privacy [35].
B. Ethical AI: Ethical AI refers to the design and deployment of
responsible and transparent AI systems in which biases are
minimized and decisions are made based on ethical principles.
In the context of IoT security, ethical issues are crucial,
including ensuring that user privacy is not violated by security
solutions. Also, impartiality and fairness in AI models must
be observed to ensure that no group or individual is unfairly
deprived of services [36]. Therefore, continuous research and
development in this field is crucial to identify and address
ethical concerns and build trust in AI-based security solutions.
This research will not only improve cybersecurity but also
increase awareness and education of users.
Proposing a High-level Strategy to Secure IoT Devices by Employing AI-Driven Decisions
Maintaining the security of connected devices is of utmost importance in the ever-changing IoT environment. Sometimes, conventional security measures are not sufficient in IoT settings due to their variety, dynamic nature, and size. The present section suggests a comprehensive, high-level technique to protect IoT devices that incorporates AI-driven judgments. Artificial intelligence can be used to enhance security measures across a variety of domains, from incident response to authentication, and present robust protection against emerging threats. The plan is focused on critical areas in which artificial intelligence may add significant value, e.g., secure communication, device authentication, intrusion detection, frequent updates, privacy protection, risk assessment, continuous development, and incident response (Figure 1).
Figure 1:Strategy for securing IoT devices.
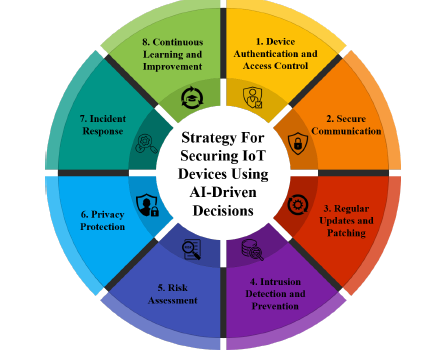
a. Use strong authentication protocols: Use strong
authentication protocols to secure IoT devices. By leveraging
AI features, it is possible to learn the typical behaviors of each
device and identify irregular authentication patterns, such as
irregular logins.
b. Secure communications: All data transfers between servers
and IoT devices should be fully encrypted. AI can help identify
unexpected patterns in network traffic, which are a sign of a
security concern and potential threat.
c. Regular updates and patches: IoT devices should be updated
regularly to ensure their security. AI can analyze historical data
to identify the most vulnerable devices and prioritize them for
updates.
d. Intrusion Prevention and Detection: Intrusion Detection
Systems (IDS) equipped with AI can detect and respond
to attacks in real time. These systems should be able to use
machine learning to detect new threats.
e. Risk assessment: Using AI to assess risks based on parameters
such as device type, location, activity, etc. can help identify
potential vulnerabilities and provide necessary preventive
measures.
f. Privacy protection: Effective measures can be taken to
protect the privacy of data collected by IoT devices using AI.
AI algorithms can be used to anonymize data and remove
personally identifiable information (PII).
g. Incident response: A comprehensive strategy should be
developed for responding to security incident events. AI can
be very effective in analyzing the incident situation and in
deciding on the best course of action.
h. Continuous learning and reinforcement: AI models must
continually learn from new data collected and refine their
predictions and conclusions. This requires a feedback loop
in which judgments about AI results are used to improve the
model (Figure 1).
For example, for better efficiency, a multilayer hybrid system
can be proposed that works as follows:
A. Step 1: Using lightweight techniques such as PCA for initial
data processing (including various features such as network
traffic, temperature, voltage, device timing, and the like) and
identification of obvious anomalies.
B. Step 2: Sending the output data of the first layer to more
complex models such as RNN or GAN for deeper pattern
analysis and accurate identification of advanced threats.
C. Step 3: Using transfer learning methods as well as edge
computing to reduce processing pressure and improve
efficiency (Resource optimization).
Future Directions
The topic of AI-based IoT security is rapidly growing and offers a number of interesting topics for future development and study. Topics include: Explainable Artificial Intelligence, federated learning, and quantum machine learning. Explainable Artificial Intelligence (XAI) aims to create AI models that provide understandable and explicit explanations for their actions. This is a critical issue for trust and understanding of AI-based security solutions. XAI research aims to improve the transparency and usefulness of AI in security applications. Federated learning, as a distributed machine learning method, enables collaborative model training while protecting data privacy [37,38]. Future research will focus on improving the scalability and efficiency of federated learning techniques and solving problems related to data connectivity and heterogeneity. Quantum Machine Learning (QML) has the potential to transform AI by extending its computational potential beyond traditional systems and could provide new answers to IoT security concerns, including rapid anomaly detection and pattern recognition. Ongoing research is studying the integration of quantum computing with artificial intelligence to improve security.
Conclusion
The rapid expansion and diversity of Internet of Things (IoT) devices pose significant security challenges due to the increasing attack surface and resource constraints. IoT ecosystems, from lowpower sensors to complex machines, have become increasingly dynamic, which complicates the implementation of traditional security methods. In the meantime, innovative solutions based on advanced technologies, especially artificial intelligence, seem essential to address these challenges. Artificial intelligence-based strategies, such as Reinforcement Learning (RL), Deep Learning (DL), and Explainable Artificial Intelligence (XAI), have opened new horizons for strengthening IoT security. These technologies have the ability to analyze huge amounts of data, identify threats in real time, and optimize security policies to suit dynamic environments. For example, reinforcement learning enables the generation of adaptive security rules, while deep learning is able to detect anomalies and react to complex patterns that indicate potential attacks. In addition, Explainable Artificial Intelligence (XAI) increases user and operator trust by providing transparent and understandable models, paving the way for more informed security decisions. This combination of technologies also enables the use of mathematical models to optimize algorithms, calculate anomaly scores, and predict attack paths based on historical data. These solutions not only reduce the complexity of IoT security, but also create infrastructures that are more resilient to cyber threats. Therefore, the application of these advanced technologies transforms IoT systems into more stable and secure structures, while ensuring the integrity, availability, and confidentiality of information (the CIA triangle). With continuous development and research in this area, we can not only stay ahead of the growing threat landscape, but also be able to effectively deal with emerging security complexities and achieve a more secure future in the IoT.
References
- Sicari S, Rizzardi A, Grieco L, Coen-Porisini A (2015) Security, privacy and trust in internet of things: The road ahead. Computer Networks 76: 146-164.
- Zaman S, Alhazmi K, Aseeri M, Ahmed MR, Khan RT, et al. (2021) Security threats and artificial intelligence-based countermeasures for internet of things networks: A comprehensive survey. IEEE Access 9: 94668-94690.
- Malik R, Singh Y, Sheikh ZA, Anand P, Singh PK, et al. (2022) An improved deep belief network ids on IoT-based network for traffic systems. Journal of Advanced Transportation 2023(1): 1-18.
- Bertino E (2016) Data security and privacy in the IoT. EDBT pp. 1-3.
- Radoglou-Grammatikis PI, Sarigiannidis P, Moscholios I (2019) Securing the internet of things: Challenges, threats and solutions. Internet Things 5: 41-70.
- Gritti C, Regnath E, Steinhorst S (2021) Practical and scalable access control mechanism for the internet of things using time-bound attribute-based encryption IACR. Cryptol. ePrint Arch 2021: 140.
- Alaba FA, Othman M, Hashem IAT, Alotaibi F (2017) Internet of things security: A survey. J Netw Comput Appl 88: 10-28.
- Conti M, Dehghantanha A, Franke K, Watson S (2018) Internet of things security and forensics: Challenges and opportunities. Future Generation Computer Systems 78: 544-546.
- Xu R, Chen Y, Li X, Blasch E (2022) A secure dynamic edge resource federation architecture for cross-domain IOT systems. 2022 International Conference on Computer Communications and Networks (ICCCN), Honolulu, HI, USA.
- Zhou J, Cao Z, Dong X, Vasilakos AV (2017) Security and privacy for cloud-based IoT: Challenges. IEEE Communications Magazine 55(1): 26-33.
- Qu Y, Yu S, Zhou W, Peng S, Wang G, et al. (2018) Privacy of things: Emerging challenges and opportunities in wireless internet of things. IEEE Wireless Communications 25(6): 91-97.
- Hashemi S, Shams F (2016) Security capabilities and vulnerabilities of internet of things architectures and the necessity of using dynamic security for IoT.
- Stoyanova M, Nikoloudakis Y, Panagiotakis S, Pallis E, Markakis E (2020) A Survey on the Internet of Things (IoT) forensics: challenges, approaches, and open issues. IEEE Communications Surveys & Tutorials 22(2): 1191-1221.
- Zia T, Liu P, Han W (2017) Application-specific digital forensics investigative model in Internet of Things (IoT). Proceedings of the 12th International Conference on Availability, Reliability and Security 55: 1-7.
- Mishra N, Pandya S (2021) Internet of things applications, security challenges, attacks, intrusion detection, and future visions: A systematic review. IEEE Access 9: 59353-59377.
- Kanimozhi V, Prem Jacob T (2021) Artificial Intelligence for anomaly detection by employing deep learning strategies in IoT networks using the trendy IoT-23 big data from Google’s tensorflow2.2. Research Square.
- Rihan SDA, Anbar M, Alabsi BA (2023) Approach for detecting attacks on IOT networks based on ensemble feature selection and deep learning models. Sensors (Basel, Switzerland) 23(17): 7342.
- Munir M, Siddiqui SA, Dengel A, Ahmed S (2019) DeepAnT: A deep learning approach for unsupervised anomaly detection in time series. IEEE Access 7: 1991-2005.
- Odeh A, Abu Taleb A (2023) Ensemble-based deep learning models for enhancing IoT intrusion detection. Applied Sciences 13(21): 11985.
- Mudgerikar A, Bertino E, Lobo J, Verma D (2021) A security-constrained reinforcement learning framework for software defined networks. ICC 2021-IEEE International Conference on Communications, Montreal, Quebec, Canada.
- Uprety A, Rawat DB (2020) Reinforcement learning for IoT security: A comprehensive survey. IEEE Internet of Things Journal 8(11): 8693-8706.
- Moerland TM, Broekens J, Plaat A, Jonker CM (2023) Model-based reinforcement learning: A survey. Foundations and Trends® in Machine Learning 16(1): 1-118.
- Li T, Zhu K, Luong NC, Niyato D, Wu Q, et al. (2021) Applications of multi-agent reinforcement learning in future internet: A comprehensive survey. IEEE Communications Surveys & Tutorials 24(2): 1240 -1279.
- HaddadPajouh H, Dehghantanha A, Khayami R, Choo KKR (2018) A deep recurrent neural network-based approach for internet of things malware threat hunting. Future Generation Computer Systems 85: 88-96.
- T Li, Sahu AK, Talwalkar Ameet, Smith V (2020) Federated learning: Challenges, methods, and future directions. IEEE Signal Processing Magazine 37(3): 50-60.
- Wang C, Wang B, Liu H, Qu H (2020) Anomaly detection for industrial control system based on autoencoder neural network. Wireless Communications and Mobile Computing 2020: 8897926:1-8897926:10.
- Ong KSH, Wang W, Hieu NQ, Niyato D, Friedrichs T (2022) Predictive maintenance model for IIoT-based manufacturing: A transferable deep reinforcement learning approach. IEEE Internet of Things Journal 9(17): 15725-15741.
- Bikmukhamedov RF, Nadeev AF (2019) Lightweight machine learning classifiers of IoT traffic flows. In 2019 Systems of Signal Synchronization, Generating and Processing in Telecommunications (SYNCHROINFO), Russia, pp. 1-5.
- Chen J, Chen S, Wang Q, Cao B, Feng G, et al. (2019) iRAF: A deep reinforcement learning approach for collaborative mobile edge computing IOT networks. IEEE Internet of Things Journal 6(6): 7011-7024.
- Upadhyaya P, Ruchi, Dutt S (2022) Transfer learning approach for 6G-IoT applications. 2022 7th International Conference on Communication and Electronics Systems (ICCES), Coimbatore, India, pp. 421-424.
- Dong H, Kotenko I (2023) An autoencoder-based multi-task learning for intrusion detection in IOT networks. 2023 IEEE Ural-Siberian Conference on Biomedical Engineering, Radioelectronics and Information Technology (USBEREIT), Yekaterinburg, Russia, pp. 1-4.
- Li FQ, Zhao RJ, Wang SL, Chen LB, Liew AWC, et al. (2022) Online intrusion detection for internet of things systems with full bayesian possibilistic clustering and ensembled fuzzy classifiers. IEEE Transactions on Fuzzy Systems 30(11): 4605-4617.
- Barry M, El Jaouhari S, Bifet A, Montiel J, Guerizec E (2022) StreamFlow: A system for summarizing and learning over industrial big data streams. 2022 IEEE International Conference on Big Data (Big Data), Osaka, Japan, pp. 2198-2205.
- Ruzafa-Alcazar P, Fernandez-Saura P, Marmol-Campos E, González-Vidal A, Hernández-Ramos JL, et al. (2023) Intrusion detection based on privacy-preserving federated learning for the industrial IoT. IEEE Transactions on Industrial Informatics 19(2): 1145-1154.
- Gupta N (2023) Artificial intelligence ethics and fairness: A study to address bias and fairness issues in AI systems, and the ethical implications of AI applications. Revista Review Index Journal of Multidisciplinary 3(2): 24-35.
- Jiang F, Fu Y, Gupta B, Liang Y, Rho S, et al. (2020) Deep learning based multi-channel intelligent attack detection for data security. IEEE Transactions on Sustainable Computing 5(2): 204-212.
- Oseni A, Moustafa N, Creech G, Sohrabi N, Strelzoff A, et al. (2023) An explainable deep learning framework for resilient intrusion detection in IoT-enabled transportation networks. IEEE Transactions on Intelligent Transportation Systems 24(1): 1000-1014.
- Benaddi H, Jouhari M, Ibrahimi K, Benslimane A, Amhoud EM (2022) Adversarial attacks against IoT networks using conditional GAN based learning. 2022 IEEE Global Communications Conference (GLOBECOM), Brazil, pp. 2788-2793.
© 2025 Masoud Hayeri Khyavi. This is an open access article distributed under the terms of the Creative Commons Attribution License , which permits unrestricted use, distribution, and build upon your work non-commercially.
 a Creative Commons Attribution 4.0 International License. Based on a work at www.crimsonpublishers.com.
Best viewed in
a Creative Commons Attribution 4.0 International License. Based on a work at www.crimsonpublishers.com.
Best viewed in 







.jpg)






























 Editorial Board Registrations
Editorial Board Registrations Submit your Article
Submit your Article Refer a Friend
Refer a Friend Advertise With Us
Advertise With Us
.jpg)






.jpg)














.bmp)
.jpg)
.png)
.jpg)










.jpg)






.png)

.png)



.png)






