- Submissions

Full Text
COJ Robotics & Artificial Intelligence
Security Concerns in Electronic Files Authenticated Systems
Femi Temitope Johnson1*, Elugbadebo Oladapo Joseph2 and Akande Adenike Folasade3
1Department of Computer Science, Federal University of Agriculture, Abeokuta, Nigeria
2Department of Computer Science, Federal College of Education, Abeokuta, Nigeria
3Department of Computer Science, Babcock University, Ilishan-Remo, Nigeria. Abeokuta, Nigeria
*Corresponding author: Femi T Johnson, Federal University of Agriculture, Abeokuta, Nigeria
Submission: January 22, 2024;Published: January 31, 2024

ISSN:2832-4463 Volume3 Issue3
Abstract
Traditional file management systems and manual processes have presented a number of difficulties and restrictions, such as difficult administration, inadequate security, and restricted data sharing options for users and organizations. After overcoming these obstacles, file management systems have typically moved to the more advanced models of today, which offer better features and benefits, particularly in critical areas where their applications cannot be compromised. The primary goal of this paper is to expound on the security concerns risks, issues associated with the traditional file systems and to highlight the benefits of implementing contemporary security measures for better data and information security in files authenticated systems.
Keywords:File encryption; Security; Management Concerns; Decryption; Algorithms
Introduction
The essential elements of our contemporary society are data and information. Their constant generation and regular interval utilization are indispensable to our day-to-day existence and decision-making processes. These days, a variety of data and databases are used by people [1], institutions and organizations in their daily lives and activities, such as phone directories, library catalogs, and dictionaries. Real-time use of blogs, WhatsApp, Facebook, Twitter, LinkedIn, and other websites on the Internet is one of the well-known means used globally for constant generation of data and information.
Figuring out how to stop illegal usage, safeguard, protect and prevent unauthorized access [2,3] to these sensitive, valuable and indisputable data while maintaining their integrity has occupied the heart of not only the organization users but also the security experts and researchers in the information security [4,5] space with topmost priority. They have continuously improved data security practices techniques to protect digital information from forgery, theft, corruption, and unauthorized access [6-8] throughout its entire lifecycle. The adopted methods cover major facets of data and information security, including administrative and access controls, logical security of software programs using cloud security frameworks and features, and physical security of hardware and storage devices [9,10].
Furthermore, a welcome development for the storage of information in cloudlets is made possible through cloud computing and its implementation methods. This makes it feasible to analyze the data using a variety of methods and produce quick results due to its associated characteristics (velocity, volume, value, variety, and veracity). The implementation of these contemporary methods for information storage and retrieval though seems to be effective [11,12] but have not totally eliminated associated risks or difficulties especially in bio-metric authentication systems [13].
Literature Review
One of the first attempts to computerize the manual filing system used in organizations for information storage was the adoption of the file processing system. The system helps in keeping computer files and the information they hold in a well-organized format to enable easy access and retrieval. They also use drives for storage and maintain the physical location of the files [14] unlike the traditional format where records and information are kept in different files and can be easily altered without detection [15].
In a quantitative study on the security of library information, Ariff et al. [16] involved two hundred and twenty-two university libraries in Pakistan. It was found that the majority of libraries did not have the common security procedures in place to safeguard their electronic records. During the digitization process of library content, certain users, particularly librarians who meet the requirements for responding to a 5-likert scale questionnaire, failed to address library vulnerability issues, putting them at risk.
The Authors in [17] presented an entropy and n-gram-based approach for the detection of malicious files. Their belief stemmed from the simple observation that any file that has been exploited should have less randomness than the original file. The proposed belief was examined using three distinct files. The findings indicated that a file’s level of randomness decreases with a lower entropy value, and that overwritten data is almost always present in large quantities over a brief period of time, alerting formal investigators to the presence of corruption in a file. Restricting file access can help prevent unauthorized access to sensitive information. Researchers [18] created a window-based application that included user device privilege control mechanisms with distinct identifiers for both standalone and networked systems in order to support his claim. They tested a variety of file formats, including image, video, audio, and presentation files. The technique made it possible for files to be secured and protected in exactly 18.5 seconds.
In order to achieve and guarantee effective performance, many organizations that face difficulties implementing file security techniques frequently opt for one or more trade-offs [19]. It was observed that the trade-offs have resulted in an unbalanced realworld performance, functionality, and security requirements. In order to balance file performance, functionality, and security, they also created a file security system that makes use of trusted execution environments (TEEs) and shielded execution. Users and organizations are turning to cloud storage as a more secure method of sharing and storing data since its introduction. A file access control system with three phases of updating key signatures that can be used to grant or deny access to hosted files was proposed [20]. They modified the deferred re-encryption and revocation scheme to assess how well their suggested techniques worked. It was found that, despite offering a high rate of access revocation, it was only applicable to social network files.
Limitations of conventional file-based approach and benefits of database inclusion in management system
Considering the overall advantages of digitalization and the use of electronic file management systems [21,1] for file storage and retrieval, one may conclude that it contributes to calming alleviation of the tension and constraints of traditional file management with the following limitations.
Data Redundancy and inconsistency: The primary source of data redundancy and inconsistency in processing systems is the needless duplication of data files [2]. It may require more resources (storage space, time and money) and more work must be done to maintain the most recent versions of all files. Multiple files containing the same data do not get updated simultaneously in traditional file processing systems due to over-existence and duplication of data. This causes inconsistencies, conflict issues and compromises the accuracy of the data as a whole [22]. These disparities eventually erode the quality of the data file’s content, which has an impact on the processing system’s ability to generate accurate reports.
Poor Data Control and security: A traditional file system is decentralized by nature because the centralized control over data elements is often times not enforced. This leads to poor data control and security which also makes it difficult to enforce security checks and access rights because application programs are added on an as-needed basis.
Data and Program Dependence: Applications and programs in file processing systems are dependent on both data and programs. The requirements of the specific application determine the physical location, organization, and retrieval of files from the storage media. When there is a change in the format or structure of data and records in a file, the reports generated typically don’t match. Either user must manually gather the necessary data or complex programs must be developed to retrieve data from every file.
Absence of sharing data Integration and the capacity for integration: Users encounter difficulties obtaining information that necessitates accessing data stored in multiple files [23] because independent data files exist. The traditional file system offers few options for sharing data, every application has its own private files, and users are not given many options when it comes to sharing the data with other apps.
One way to get around the limitations of the traditional file
processing methods was to implement a basic database provision
and inclusion. According to Cherry et al. [24] databases help with
precise data management [24] and ensure that all data files are
updated immediately after system updates. Other advantages of
using databases in file management systems are as follows:
A. Data Independence and consistency: The effects of
data redundancy are reduced in database managed systems.
Programs that access the data are not impacted by modifications
to the database structure because the data files are stored in a
way that allows for this. Once every occurrence of a data item in
the processing system has been recorded, there is no risk of one
system updating the item while another does not.
B. Improved security, control and integrity of Data: The
database administrators set up the database according to
security requirements and manages who can access what
information [25] With the help of a validation routine or by
making the entry of one or more fields mandatory, users of the
DBMS can impose restrictions on data [26]. It can guarantee
that access to the data is restricted to authorized users only.
C. Data Accessibility and Enhanced Productivity: More
data, formerly kept on disparate departments’ and sometimes
incompatible platforms’ systems, is now available to users.
Besides, it provides an easy-to-use query language so that users
can query and get responses right away without having to pay a
programmer to write the queries.
Encryption for Security Measures in File Management Systems
Preventing unauthorized users from stealing, altering, or erasing private information is enforced in encryption. During the encryption process, data is converted into cipher text and could be stored in a database [27] making it accessible to only users who possess the secret key to decrypt it. This is done by using a mathematical function to generate secret keys using one, two, or more algorithms. The user can request plain text when they want it by using decryption algorithms to extract cipher texts saved in the database. These algorithms can be used with the same key (symmetric method) or different keys (asymmetric method) used for encryption (Figure 1).
Figure 1:Encryption processes framework in database file management systems.
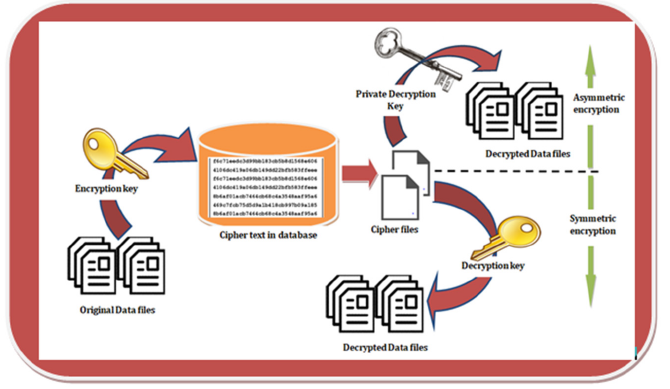
In addition, deploying hashing and encryption in a database limit access through authentication and authorization. Even with access to the database, an intruder cannot access the data if it has been properly encrypted before being saved in the database. A user can be assisted in creating a fixed-length value that condenses the contents of a file or message used in database-managed systems by deploying hashing techniques that make use of developed functions and algorithms. Database encryption also seeks to guarantee the proper use of data. The database structure needs to be carefully considered from the beginning, with security precautions supplied with keys at every development stage. It is simpler for unauthorized users to decrypt and access the database if all of the database’s keys are the same.
Consequently, it is also necessary to match distinct corresponding keys to the various database sections and units. Several authors have used one or more of these methods to develop cryptography and digital signatures that impose integrity controls for better message and file security [4,15,28].
Another security measures for file management is Software encryption. Software development requires a lot of time in investment [29]. One common method of encrypting software is the provision of a combination of automatically generated codes in the form of serial numbers. Additional techniques is the adoption of internet facilities for software serial numbers of transfers through service providers with data encryption technology to create the serial number or registration code with the corresponding host ID.
Ensuring the authenticity of the transaction object and the total security of user data are very crucial for organization, especially in e-commerce. Although some unwanted activities by potential users may inevitably occur to circumvent the security measures put in place, the e-commerce application’s security can be enhanced by the efficacy of digital signatures that encrypt user information and make them to be un-accessible to others. Furthermore, this public key can be used by the digital certification institution to decode the receiver’s data and digital signature, identify any denial behavior, and take quick action to stop an attack.
Biometric systems for modern file security
Biometric data and systems are commonly used in security devices and are applied in systems that attempt to identify a specific user or other human through unique characteristics [30]. These systems depend on large amount of data [31] and rely on complex algorithms to sort and uniquely distinguish among multiple collected data to achieve an identifying result in a given application [32]. Biometric recognition is a challenging task but the human brain can carry out this incredibly complex process.
In spite of the fact that there have been several complaints about
how trustworthy biometric authentication could be [33], other
security measures have continuously been incorporated, setting
them apart from more conventional password, PIN, or token-based
authentication technologies [34]. The operational principles of
biometric systems rely on two distinct processes: enrollment and
recognition. At the enrollment phase, user’s characteristics are
captured, processed, and stored for later use in embedded systems.
The enrollment procedures are highlighted below as.
A. The input signal is acquired by means of a biometric
scanner. When the quality of the sensed signal is checked
and found below a threshold it becomes rejected and a new
acquisition is performed to fit the system.
B. The required data is extracted from the input signal by
means of digital signal processing techniques.
C. Measured parameters and features from the data
are stored and used for the modeling of each individual
recognizable attribute. In addition, at the recognition mode,
extracted features are compared with input signals from which
access will be granted. Occasionally, access may be denied
when the model fails to generate features for identification that
would increase the Failure to Enroll (FTE) rate.
D. The second phase is the Recognition phase: Once the
user is enrolled, the system can then proceed with the user
identification or verification mode.
Security and privacy concerns for biometric systems
One of the astonishing features about biometric security systems is that users may be assigned equal level of access with or different level of privilege [35] depending on the user roles which makes it possess some level of security. When the hacker’s goal of deciphering the password of at least one worker or user is accomplished, he is able to utilize all of the system’s resources. This could also lead to overall security compromise of every system to which the user has access is compromised in this instance by a weak password.
Another concern with biometric systems is the fact that biometric data are not made secret [36] and could be difficult to replace after being compromised by a third party. Although, it may require simpler processes to rectify in some applications where the administrators can easily detect the authenticity of the data but in other internet enabled applications it could be very complex. Generally speaking, in terms of security issues, ongoing and continuous updates are required to maintain protection. Failure to update may turn the system to an obsolete type which can no longer be appropriate for the modern world. Because of this, no one can assert that they have a flawless security system or that it will endure forever.
The generation of too many false positive or negatives is also another concern in biometric based file authenticated systems. This occurs when a condition or file that exists in the system’s database is devoted to being false or has not existed. Often times, this may result in the delay of the authentication process and access to urgently needed files as repeated trials will be demanded. The aftermath effect of this may result in severe damage especially in very pressing situations involving lifesaving conditions or seeking immediate protection from attacks. During these repeated trials, the system utilizes more resources and undergoes serious trials.
Conclusion
The problems with data and file security are ever evolving. Emerging best practices and improved identification techniques of newer threats to sensitive information protection keep people and organizations on the cutting edge. The architecture of the security system and related network, along with user privileges and mission requirements, must be understood in order to take a comprehensive approach to data, file security and combat emanating threats. The use of data encryption technology is expanding and is progressively being integrated into applications and systems pertaining to other fields including finance, education, healthcare, and energy.
These applications and systems do not only offer convenient security for businesses and government organizations, but also safeguard the lives of individuals. Biometric secured systems encryption offer more reasonable security features than password or pin secured systems. With this advantage, it is obvious that biometric systems with improved security features have begun to govern the security domain in our present days but the speed and accuracy of authentication is still worth looking into for improved solution.
References
- Deb K (2014) Multi-objective optimization. In: Search Methodologies: Introductory Tutorials in Optimization and Decision Support Techniques, Springer, Boston, Massachusetts, USA, pp. 403-449.
- Faccio M, Granata I, Menini A, Milanese M, Rossato C, et al. (2022) Human factors in cobot era: A review of modern production systems features. J Intell Manuf 34: 85-106.
- Kanazawa A, Kinugawa J, Kosuge K (2019) Adaptive motion planning for a collaborative robot based on prediction uncertainty to enhance human safety and work efficiency. IEEE Transactions on Robotics 35(4): 817-832.
- Romero D, Stahre J (2021) Towards the resilient operator 5.0: The future of work in smart resilient manufacturing systems. Procedia CIRP 104: 1089-1094.
- Zanchettin AM, Rocco P, Chiappa S, Rossi R (2019) Towards an optimal avoidance strategy for collaborative robots. Robotics and Computer-Integrated Manufacturing 59: 47-55.
© 2023 Shady Saikali. This is an open access article distributed under the terms of the Creative Commons Attribution License , which permits unrestricted use, distribution, and build upon your work non-commercially.
 a Creative Commons Attribution 4.0 International License. Based on a work at www.crimsonpublishers.com.
Best viewed in
a Creative Commons Attribution 4.0 International License. Based on a work at www.crimsonpublishers.com.
Best viewed in 







.jpg)






























 Editorial Board Registrations
Editorial Board Registrations Submit your Article
Submit your Article Refer a Friend
Refer a Friend Advertise With Us
Advertise With Us
.jpg)






.jpg)














.bmp)
.jpg)
.png)
.jpg)










.jpg)






.png)

.png)



.png)






